Navigating Cybersecurity Frameworks and Regulations - A Cybersecurity Architect's Perspective
This blog explores how cybersecurity architects can align key frameworks and regulations — including NIST CSF v2.0, DORA, NIS2, ISO 27001:2022, and CIS Controls v8 — with Microsoft Defender and Sentinel. Gain insights into strategic integration for governance, compliance, and operational monitoring.
Navigating Cybersecurity Frameworks and Regulations: A Cybersecurity Architect’s Perspective
Introduction
Designing a security architecture is more than just implementing the latest tech — it’s about aligning technical capabilities with strategic governance. As architects, we often find ourselves balancing business expectations, regulatory mandates, and threat landscapes. The common thread that ties them together? Security Governance.
In this post, we’ll look at how to map five influential frameworks and regulations to your architecture strategy — and how Microsoft Defender and Sentinel can help streamline this journey.
Why These Frameworks and Regulations?
As a Microsoft Security Architect, I regularly work with organizations that rely on the Microsoft 365 Defender and Microsoft Sentinel ecosystem. Choosing frameworks like NIST CSF, DORA, NIS2, ISO 27001:2022, and CIS Controls v8 wasn’t accidental — they are directly aligned with Microsoft’s native capabilities, and more importantly, they help stakeholders understand how governance connects to day-to-day detection and response.
Here’s why each one matters in practice:
🔍 NIST CSF v2.0
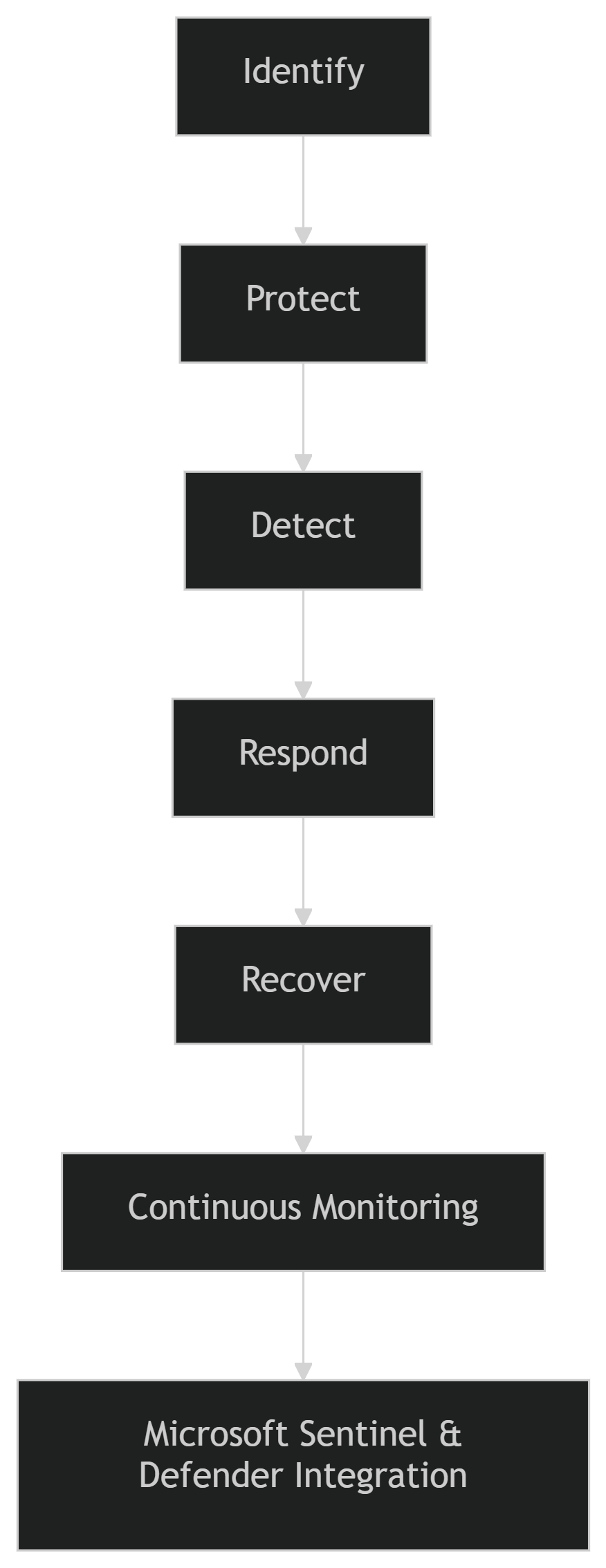
NIST is Microsoft’s foundational cybersecurity framework. It’s deeply embedded in products like Defender for Cloud, which provides compliance insights mapped to NIST controls out of the box. This framework also resonates well with customers outside the U.S. due to its clear structure (Identify, Protect, Detect, Respond, Recover) and compatibility with operational tools like Microsoft Sentinel and Microsoft Defender for Endpoint.
Use Case:
When onboarding customers to Sentinel, we often structure analytic rules, workbooks, and playbooks based on NIST CSF categories — making it easier to communicate technical controls to risk and compliance teams.
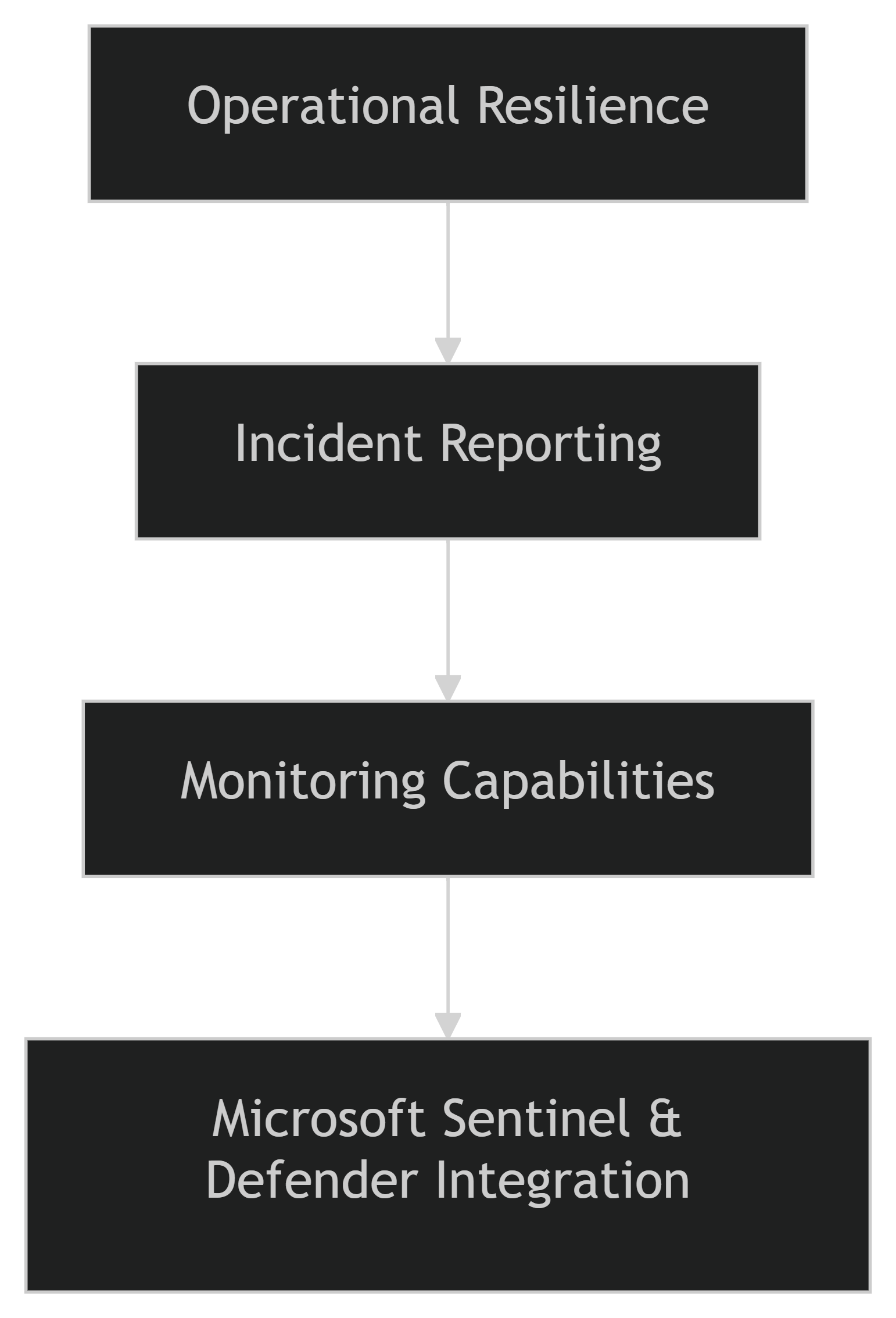
💼 DORA
DORA is becoming a major driver in the EU financial sector, pushing teams to formalize operational resilience and incident reporting. With Microsoft 365 Defender, organizations can automate incident correlation across endpoints, identities, and cloud apps — aligning perfectly with DORA’s demand for cross-platform resilience and incident response workflows.
Use Case:
For a European bank, we configured Defender for Identity and Microsoft Sentinel to auto-escalate high-risk detections to the SOC, while maintaining reporting dashboards for auditors — satisfying both operational and compliance needs.
🛡️ NIS2
NIS2 increases the baseline for security maturity, especially for essential entities operating in Europe. This directive aligns well with Defender for Cloud, Defender for Servers, and Sentinel, which together offer telemetry, cloud hygiene, and incident management across hybrid environments.
Use Case:
A logistics provider subject to NIS2 used Defender for Endpoint for endpoint detection, Defender for Cloud Apps for shadow IT discovery, and Sentinel to unify their threat picture.
🌐 ISO/IEC 27001:2022
ISO 27001 provides a structured way to build an Information Security Management System (ISMS). Microsoft provides support through compliance manager, Purview, and Sentinel auditing and monitoring features. It’s especially useful for showing risk treatment and governance to executive boards.
Use Case:
A multinational enterprise used Microsoft Purview to handle information classification and Sentinel to detect policy violations, helping them demonstrate ISO 27001 control coverage.
🧩 CIS Controls v8
CIS Controls offer a highly practical checklist for security teams. They are ideal for “blue team” maturity and can be directly mapped to Microsoft solutions — from Defender for Endpoint’s attack surface reduction rules, to Defender for Cloud’s security recommendations, and Sentinel’s MITRE ATT&CK rule sets.
Use Case:
We used the CIS Controls framework to assess an organization’s SOC maturity. Then we implemented Sentinel’s built-in threat detection aligned with the MITRE framework and enhanced visibility through Defender for Identity and Defender for Cloud Apps.
In short, these frameworks were chosen not just for their industry acceptance — but because they map directly to how Microsoft’s security tools work. This alignment accelerates value realization, simplifies audits, and gives clarity to both engineers and executives.
Comparison – Differences and Overlaps
| Feature | DORA | NIS2 | NIST CSF v2.0 | ISO 27001:2022 | CIS Controls v8 |
|---|---|---|---|---|---|
| Type | Regulation | Regulation | Framework | Standard | Controls |
| Sector Focus | Financial | Essential/Important Sectors | Broad | Broad | Broad |
| Governance Model | Prescriptive | Mandated Reporting | Voluntary | Structured ISMS | Tactical Baseline |
| Monitoring Emphasis | High | High | High | Medium | High |
| Integration with Microsoft Defender & Sentinel | ✅ | ✅ | ✅ | ✅ | ✅ |
Architecting Compliance with Microsoft Sentinel & Defender
Let’s look at how to pragmatically implement these frameworks and regulations using modern Microsoft tooling. Each section includes a high-level process you can customize per use case.
✅ Aligning with NIST CSF v2.0
- Use Microsoft Sentinel’s analytic rules to implement “Detect” functions.
- Configure Defender for Endpoint/Cloud/Identity to cover “Protect” and “Respond” activities.
💼 Complying with DORA
- Build incident response playbooks in Sentinel for financial sector requirements.
- Use Microsoft 365 Defender to automate reporting and notification workflows.
🏗️ Meeting NIS2 Requirements
- Leverage Microsoft Defender for Cloud and Defender for Servers for asset-level visibility.
- Implement threat intelligence ingestion in Sentinel for enhanced situational awareness.
🔒 Adopting ISO 27001:2022
- Use Microsoft Purview and Sentinel audit logs to track ISMS policy enforcement.
- Apply regulatory compliance workbook in Defender for Cloud for continuous control validation.
🧠 Implementing CIS Controls v8
- Map Sentinel analytic rules and Defender recommendations directly to CIS safeguards.
- Use Security Recommendations in Microsoft Secure Score as a CIS maturity benchmark.
Conclusion
Whether you’re working with a large European bank, a government agency, or a global manufacturer, security architects must not only speak the language of technology — but also of regulation and governance. Mapping these frameworks to your Microsoft security ecosystem empowers you to deliver both compliance and resilience.
💬 Call to Action
Have you mapped these frameworks in your organization? What challenges did you face aligning governance with detection and response?